Why Use Keystore Secrets?
Storing secrets in environment variables or.env files is common but risky:
- Environment variables can leak via process listings
.envfiles can be accidentally committed to git- Credentials scattered across multiple files are hard to audit
- Encryption at rest - Secrets encrypted by the OS
- Access control - Keystore access requires user authentication
- Centralization - All secrets in one auditable location
- Memory safety - Secrets zeroized from memory after use
Quick Start
1. Store a Secret
macOS:2. Use the Secret
$OPENAI_API_KEY.
How It Works
Storing Secrets
All nono secrets are stored under the service namenono in the system keystore.
macOS Keychain
Using the Terminal
Using Keychain Access (GUI)
You can also use the Keychain Access application to manage secrets:- Open Keychain Access (search in Spotlight or find in
/Applications/Utilities/) - Select the login keychain in the sidebar
- Click File > New Password Item (or press
Cmd+N) - Fill in the form:
- Keychain Item Name:
nono - Account Name:
openai_api_key(or your secret name) - Password: Your API key value
- Keychain Item Name:
- Click Add
- Search for
nonoin the Keychain Access search bar - Double-click an entry to view details
- Check Show password to reveal the value (requires authentication)
Avoiding Repeated Password Prompts
When nono accesses a secret for the first time, macOS will prompt you to allow access. To avoid being prompted every time:- When the access prompt appears, click Always Allow
- This grants nono permanent access to that specific secret
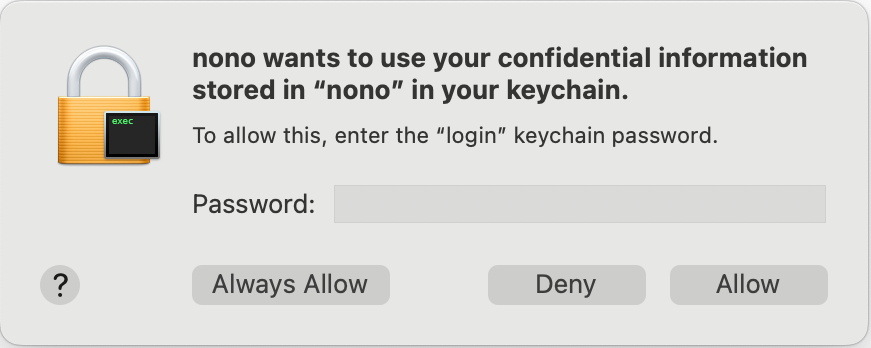
The
security command-line tool and Keychain Access both manage the same keychain. Secrets created with either method will work with nono.Linux Secret Service
Linux uses the Secret Service API, typically provided by GNOME Keyring or KWallet. You’ll needsecret-tool (part of libsecret-tools) and a running keyring daemon.
Installation
Debian/Ubuntu:Using the Terminal
Using GNOME Passwords (Seahorse)
If you have a graphical desktop, you can use the Passwords app (also called Seahorse):- Open Passwords (search in your applications menu, or run
seahorse) - Click the + button or go to Password > New
- Select Password keyring and click Continue
- Fill in the form:
- Description:
nono: openai_api_key - Password: Your API key value
- Description:
- Click Add
Using KDE Wallet (KWallet)
If you use KDE Plasma:- Open KWallet Manager from your applications menu
- Open your wallet (usually
kdewallet) - Create a new folder called
nonoif it doesn’t exist - Right-click and select New > Password
- Name it
openai_api_keyand enter your API key
KWallet stores secrets differently than GNOME Keyring. The
keyring library nono uses supports both, but the attribute format may differ. Test with nono run --dry-run to verify secrets load correctly.Using Secrets
CLI Flag
Specify comma-separated account names to load:| Account Name | Environment Variable |
|---|---|
openai_api_key | OPENAI_API_KEY |
anthropic_api_key | ANTHROPIC_API_KEY |
github_token | GITHUB_TOKEN |
Profile-Based Secrets
Profiles can declare which secrets to load in a[secrets] section:
--secrets:
[secrets] section maps keystore account names to environment variable names, giving you full control over naming.
Error Handling
Secret Not Found
Keystore Locked
Multiple Entries
Security Considerations
What nono Protects
- Keystore file access - Sandbox blocks direct access to
~/Library/Keychains(macOS) and keyring files - Memory exposure - Secrets wrapped in
Zeroizing<String>and cleared after use - Credential sprawl - Encourages centralized secret storage
Limitations
- Environment variable visibility - On Linux,
/proc/PID/environis readable by same-user processes - Malicious use of credentials - nono cannot prevent a sandboxed process from misusing legitimately obtained credentials
- Keystore security - Relies on OS keystore security
Best Practices
- Use unique account names - e.g.,
myapp_openai_keyrather than justapi_key - Rotate secrets regularly - Update keystore entries periodically
- Audit secret access - Check which profiles request which secrets
- Minimal secrets - Only grant secrets that are actually needed
Examples
Claude Code with API Keys
Custom Agent Profile
Dry Run to Check Secrets
Troubleshooting
macOS: “security: SecKeychainSearchCopyNext: The specified item could not be found”
The secret doesn’t exist. Verify the service and account names:Linux: “secret-tool: No secret found”
Ensure the secret-service daemon is running:Linux: “Cannot autolaunch D-Bus without X11”
You’re running on a headless system without a graphical session. Secret Service requires a D-Bus session. See the next section for solutions.Linux: “Cannot create an item in a locked collection”
The keyring is locked. This is common on headless servers or SSH sessions. See the next section for solutions.Headless Linux Environments
Secret Service (GNOME Keyring) can be problematic on headless servers and SSH sessions because:- It requires D-Bus session bus
- The keyring is typically locked without a graphical login
- Unlocking the keyring interactively over SSH is cumbersome
Option 1: Use pass (Recommended for Headless)
pass is the standard Unix password manager. It uses GPG encryption and works well in headless environments.
Setup:
Native
pass backend support is planned for a future release.Option 2: Environment Variables via Wrapper
For simple setups, export secrets from a protected file:Option 3: Set Up Headless Keyring
If you prefer to use Secret Service in headless mode: 1. Create an unlock script:Option 4: systemd User Service
For servers with systemd, you can run gnome-keyring as a user service:Next Steps
- CLI Reference - Complete flag documentation
- Profiles & Groups - Profile system overview